Mandry SECURE: Your Cyber Risk Management Partner
We Secure Risk to Enhance Your Peace of Mind
Security risk assessments are a great start to managing cyber risk, but they don't check all the boxes. Our experts hold various cybersecurity and regulatory compliance certifications, and our organization has multiple complementary credentials. Our goal is to provide you with peace of mind knowing your organization is secure.
- Business continuity planning
- IT compliance analysis
- Security risk assessments
- Compliance gaps remediation plan
- Cybersecurity safeguards and employee awareness training
- Anti-virus, web filtering, and spam filtering
What Mandry SECURE Provides Your Organization
Our goal is to solve all of your organization's compliance and security needs.
Visibility
We will show you the threats and risks facing your organization to help you avoid internal and external blind spots.
Prioritization
We will help you focus your resources on the threats that pose the greatest risk to your organization.
Acceleration
The objective information, operational insights, and verifiable data we provide allows you to make risk decisions at the speed of your business.
Collaboration
Our team works with your team to quickly and collectively reduce risk through education, mentoring, and implementation of remediation activities.
Validation
Our assessment of the effectiveness of existing information privacy and security governance controls will help you validate those efforts.
Identification
Our identification of your internal and external vulnerabilities and threats will help you gain a holistic view of the risks created by IT systems and practices.
Compliance
We will help you align your people, processes, and technologies with regulatory compliance frameworks and industry best practices to ensure compliance with regulatory requirements.
Maximization
Through continuous assessment, executive-level reporting, and mentoring from certified information security and privacy professionals, you will be able to maximize the value of your security risk assessments by understanding threats, prioritizing risks, and accelerating decisions.
Why Choose Us to Be the Securer of Your Cyber Risk
Systems & Processes Designed for Your Environment
Perpetual Evaluation of People, Practices, & Technology
Long-Term Partnership With a Provider Who Cares
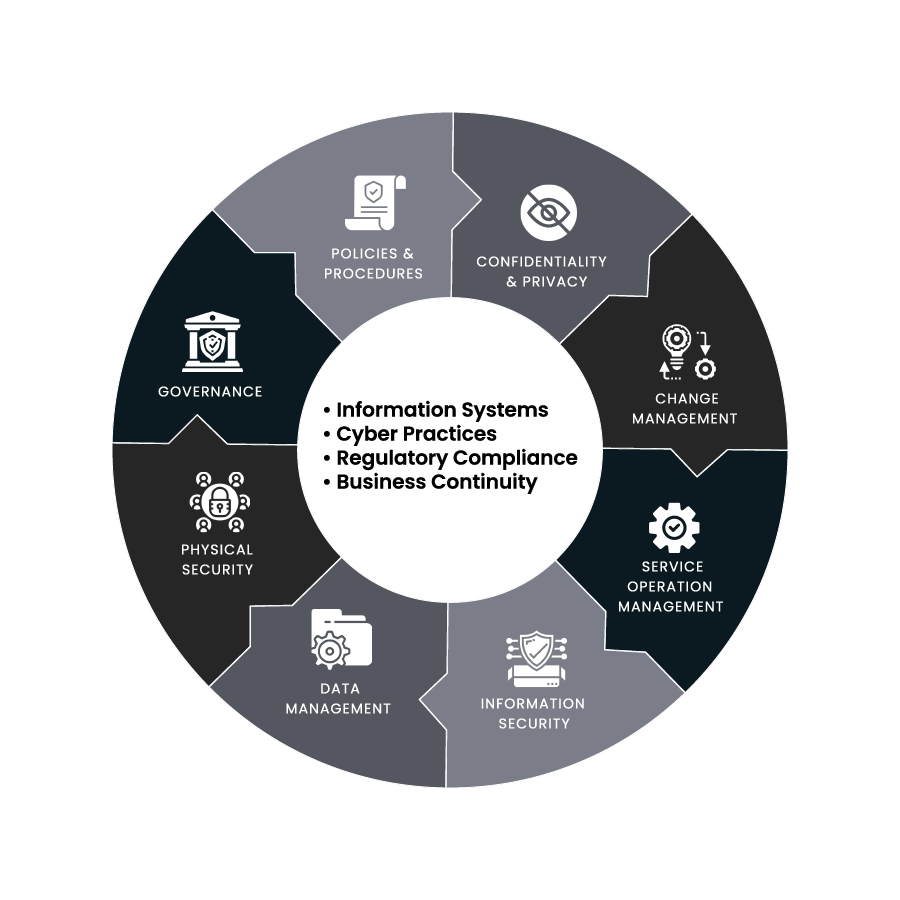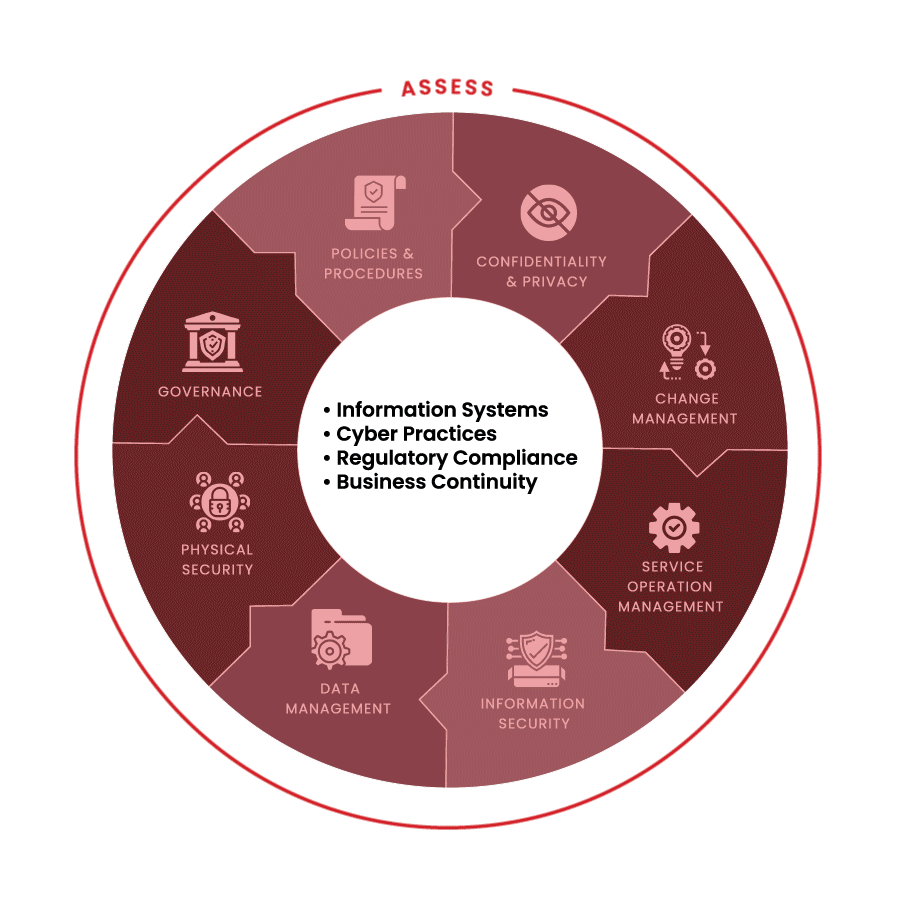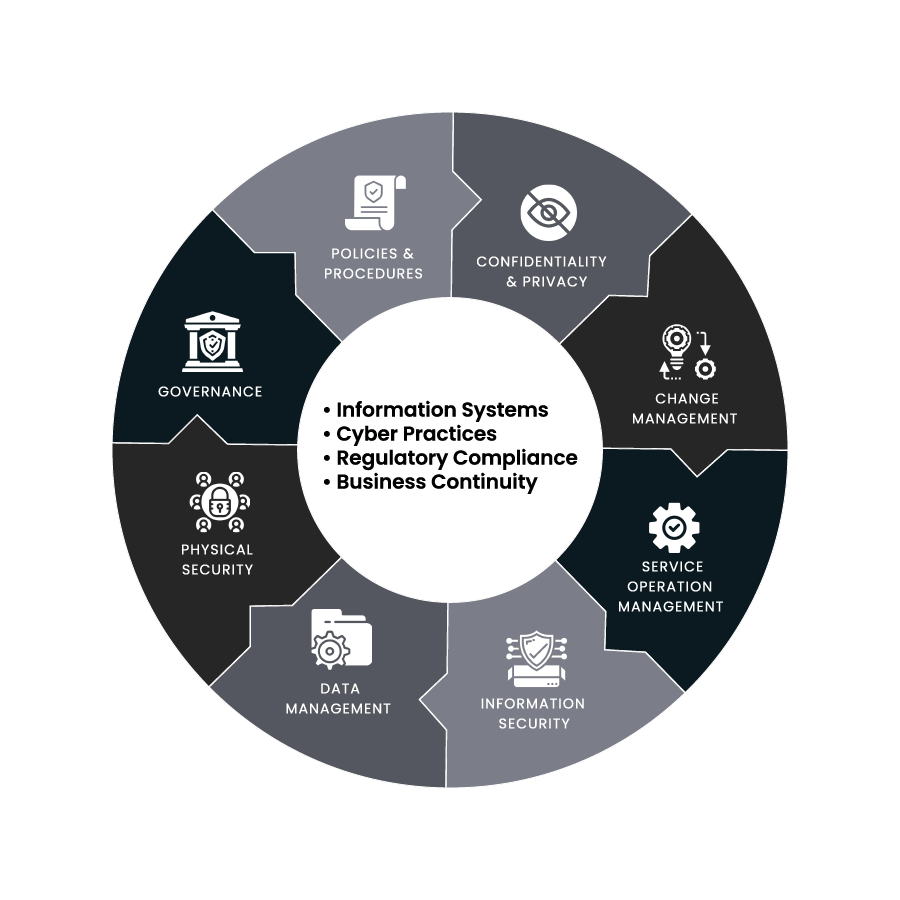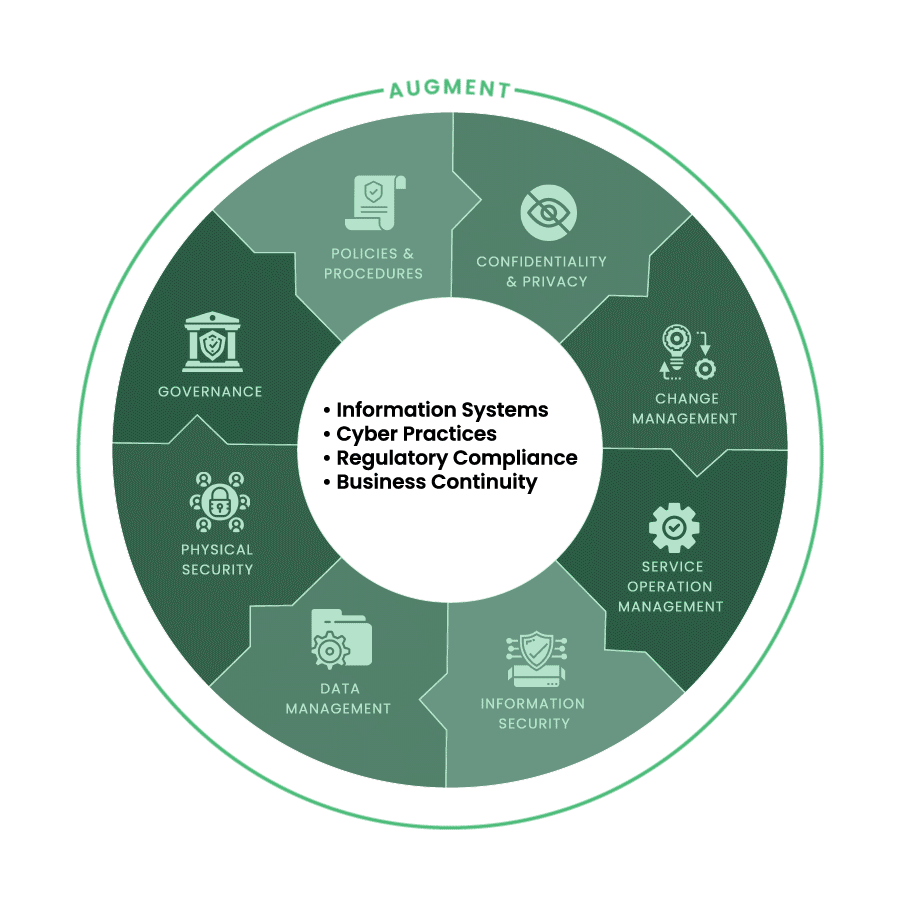
How We Expand Cyber Risk Management Beyond a Security Risk Assessment
Assess
Current state of cybersecurity protection
Advise
How to better protect your environment
Augment
Leverage shared knowledge to expand capacity and deploy solutions
Recent Cybersecurity Resources
More Mandry Services

24/7 Proactive Technologies
Reduce business disruptions and save your team unnecessary headaches with flexible and scalable IT management solutions.
VOIP Phone & Business Communication Solutions
Enhance the speed, quality, reliability, and security of all business communications.


Cloud Strategy Consulting & Architecting
Understand and roll out a full, effective, scalable cloud strategy for your business.